Secure the Supply Chain
Why choose Verus for Industrial Cybersecurity?
Verus uses cutting-edge encryption and multi-factor authentication to safeguard sensitive data from creation to disposal, ensuring trust and compliance.
Verus simplifies compliance through audit trails, real-time monitoring, and automated reporting, minimizing risks of fines and reputational harm.
Verus integrates seamlessly with existing financial systems, providing secure, anytime access to data to enhance efficiency and patient care.
Verus provides round-the-clock expert support to resolve security issues and maintain optimal performance, minimizing disruptions in critical services.
Why Supply Chain Security Matters
Interconnected networks mean a breach at one point can ripple across your business. Common risks include:
-
Third-party access vulnerabilities.
-
Unsecured data sharing.
-
Weak vendor security practices.
Verus strengthens your manufacturing vendor security with proven strategies.
Verus’ Supply Chain Protection Strategies
Our approach includes:
-
Vendor Risk Management: Assess and monitor third-party security.
-
Secure Data Sharing: Encrypt sensitive information.
-
Access Controls: Limit who can interact with your systems.
With Verus, your supply chain becomes a strength, not a liability.
Strengthen Your Supply Chain with Verus
Ready to secure your manufacturing supply chain?
Contact us for expert advice today. 1-800-958-3787
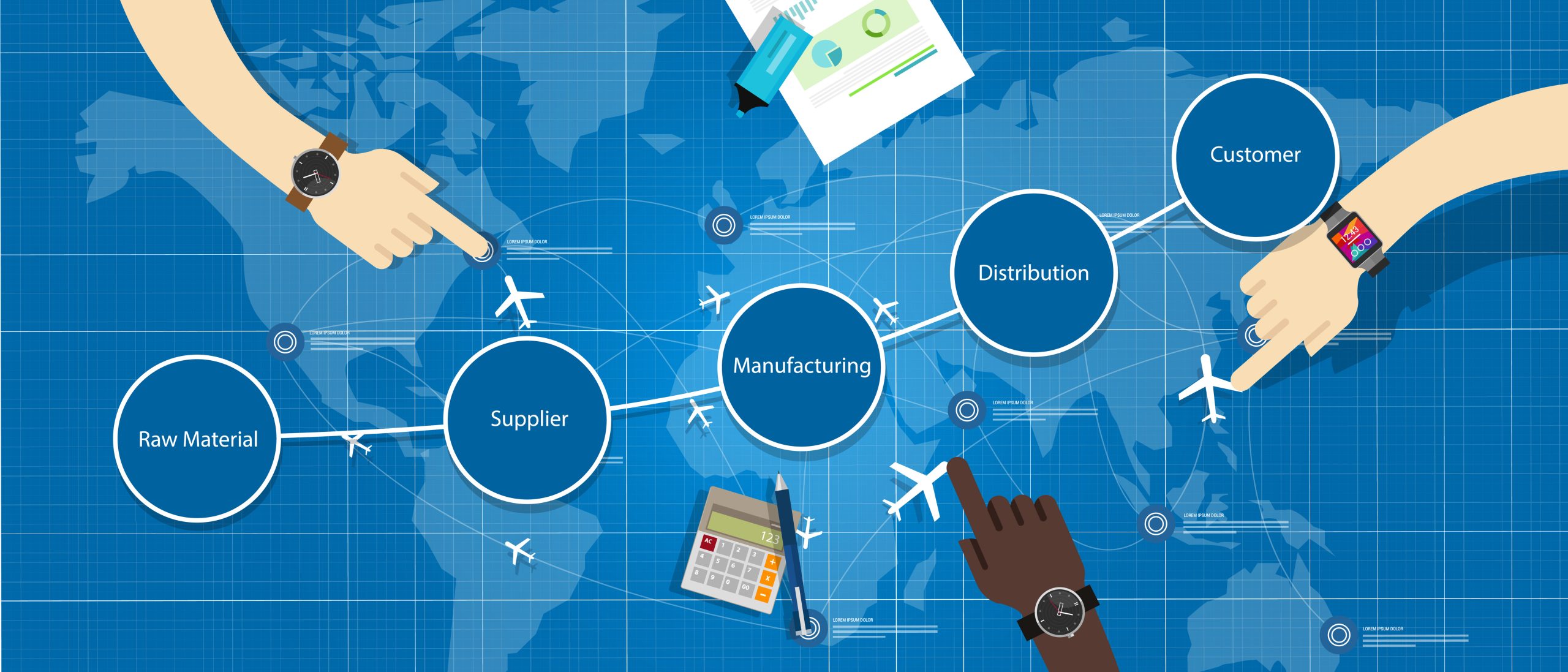
Protect your manufacturing supply chain with Verus. Learn how to secure vendor networks and prevent cyber risks effectively.
Verus is here for you.
Assisted Living
In the rapidly evolving Senior Care and Assisted Living Community landscape, organizations are embracing technology to provide exceptional care.
Energy
The quantity of cyberattacks on energy infrastructure has increased substantially, magnifying organizations’ need to protect against cyber threats.
Healthcare
In the rapidly evolving digital landscape, healthcare organizations face unique and complex challenges with regulation and patient data.
Finance
Financial institutions connect to almost every aspect of our economy and personal data, which exposes them to an enormous amount of risk.
Manufacturing
Many organizations in the manufacturing and industrial sectors underestimate the need for cybersecurity protection.
Non-Profits
In the ever-expanding digital landscape, criminals lurk around every corner. Cybersecurity is no longer optional; it is a requirement.
Hospitality
The digital threats to the hospitality indusry are increasing. Cybercriminals target private and payment data.
Insurance
Insurance companies manage vast amounts of personal and financial data, creating prime targets for cyberattacks.